Hi
I’m trying to setup the EventStore on a Windows host with an external wildcard certificate - but what should I put in the TrustedRootCertificatesPath?
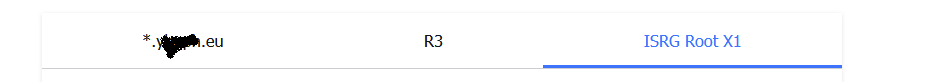
When using the online configuration tool I end up with this setting using a wildcard certificate:
TrustedRootCertificatesPath: [not provided]
But then EventStore doesn’t start!
Invalid Configuration: TrustedRootCertificatesPath must be specified unless insecure mode (--insecure) is set.
Best regards
Jens Christiansen
TrustedRootCertificatesPath: C:\ESDB\certs\ca
it’s the directory where you place the root ca you’re using
Hi Yves
But I don’t have a root ca since I’ve bought a trusted wildcard certificate.
I’d try still to point the setting to the same path as the certificate and expect that the default set of trusted root authorities will be trusted by default using the certificate store.
BTW I found this issue open since July this year. I added my comment there, I believe the setting should not be mandatory.
Exactly… that make way more sense 
By the way it doesn’t help anything pointing to the same path as my certificate!
But I don’t have a root ca since I’ve bought a trusted wildcard certificate.
If you bought a cert, you have one, and it must be downloadable or in your trusted cert store .
you only need the public key, it’s only for validation purpose.
in the case of letsencrypt in the screenshot the root is ISRG Root X1, it’s not in the full chain that they provide, but it is in my local cert store .
it’s just a matter of exporting it & transforming to PEM file and place it the directory configured in
TrustedRootCertificatesPath
if you exported in X509 DER format do this & copy root.pem
openssl x509 -inform der -in root.cer -out root.pem
Hi Yves
I have a Sectigo certificate with the current certification path:
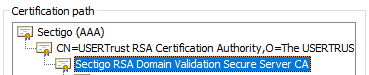
I’ve tried exporting all of the certificates in the path and convert them to PEM but I’m still getting an error starting EventStore:
Certificate with thumbprint '33E4E80807204C2B6182A3A14B591ACD25B5F0DB' does not appear to be a valid root certificate since it is not self-signed
I get the same error on all certificates in the path.
Any idea would be appreciated.
/Jens Christiansen
in the TrustedRootCertificatesPath you need only the Sectigo(AAA) public cert
.\certs
├───ca (<- the `TrustedRootCertificatesPath`
│ isrgrootx1.pem (<- the root CA of let's encrypt (in your case Sectigo(AAA))
│
└───node
fullchain.pem (`CertificateFile` , contain R3 & *.mydomain.tld
privkey.pem.key (`CertificatePrivateKeyFile` the private key of *.mydomain.ltd)
I think the point here @yves.lorphelin that every OS already has all the trusted root CA certificates built-in, and asking people to put is somewhere again is just waste of time. For example, on Linux I set this option to /etc/ssl/certs but even that should be the default. The server should not assume that people use self-signed certificates. I don’t know where this idea even came from tbh…