josh2
May 5, 2021, 9:56pm
1
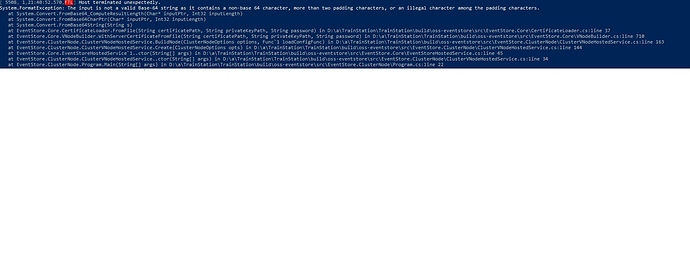
I’ve created .pem files with certbot (windows) to create ssl wildcard certification to run eventstore in secure mode. I used open ssl to convert cert.pem to node.crt and privkey.pem to node.key.
When I try to run it, setting the keys in eventstore.conf to those files I get this:
What am I missing?
Can you provide the steps you performed for creating the cert & transforming it , as well as the relevant configuration you start the database with ?
josh2
May 6, 2021, 4:40pm
3
The cert was created with certbot, using this in powershell:
certbot certonly --manual --preferred-challenges=dns --email josh@site.ca --server https://acme-v02.api.letsencrypt.org/directory --agree-tos --manual-public-ip-logging-ok -d “*.site.ca”
certificate was then transformed using:
rsa -outform der -in private.pem -out private.key
The configuration that I used is the basic one from the configuration wizard:
Paths
Db: C:\ESDB\Data
Index: C:\ESDB\Index
Log: C:\ESDB\Logs
Certificates configuration
CertificateFile: C:\ESDB\certs\cert.pem
CertificatePrivateKeyFile: C:\ESDB\certs\privkey.key
TrustedRootCertificatesPath: c:\esdb\certs
CertificateReservedNodeCommonName: “*.site.ca”
Network configuration
IntIp: 20.123.171.143
ExtIp: 20.123.171.123
IntHostAdvertiseAs: www.site.ca
ExtHostAdvertiseAs: www.site.ca
HttpPort: 2113
IntTcpPort: 1112
EnableExternalTcp: false
EnableAtomPubOverHTTP: true
Projections configuration
RunProjections: None
(You might want to remove/redact any private info above)
josh2
May 6, 2021, 5:04pm
5
I’m running a single node for now, but yes, on windows.
Hi Josh,
The only added step was to move privkey.pem to another folder has it gave an error :
what version are you on ? I tried with 20.10.2.0, which is the LTS version.
josh2
May 7, 2021, 5:46pm
7
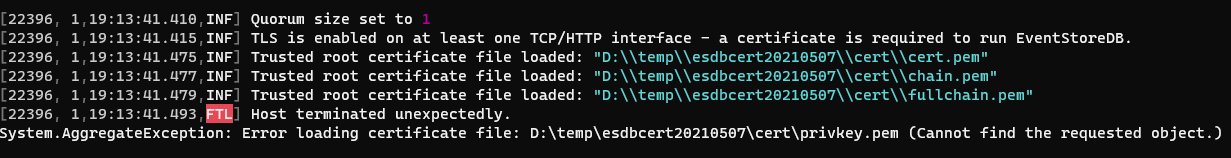
Can I see the eventstore.conf?
---
# Paths
Db: D:\temp\esdbcert20210507\Data
Index: D:\temp\esdbcert20210507\Index
Log: D:\temp\esdbcert20210507\Logs
# Certificates configuration
CertificateFile: D:\temp\esdbcert20210507\cert\cert.pem
CertificatePrivateKeyFile: D:\temp\esdbcert20210507\cert\privkey.pem.key
TrustedRootCertificatesPath: D:\temp\esdbcert20210507\cert\
CertificateReservedNodeCommonName: "*.redac.ted"
# Network configuration
IntIp: 127.0.0.1
ExtIp: 127.0.0.1
IntHostAdvertiseAs: node1.redac.ted
ExtHostAdvertiseAs: node1.redac.ted
HttpPort: 2113
IntTcpPort: 1112
EnableExternalTcp: false
EnableAtomPubOverHTTP: true
# Projections configuration
RunProjections: All
1 Like
I know that private keys generated by certbot are in a different format than ESDB expects. I have opened an issue about it a while ago.
Until it is solved (hopefully), you can convert the key to RSA key format using openssl:
openssl rsa -in privkey.key -out privkeyrsa.key
Then, use the RSA private key.
I have the same problem but, using the converted rsa key, the service still fails to start due to a “private key decode error” because the two files are the same. Is something changed during these years?
EDIT: openssl rsa -in old.key -traditional -out privkeyrsa.key
1 Like